Java生成SM2证书基于BouncyCastle(cer)
可以先加QQ 783021975 咨询相关问题。代码后续会更新一部分
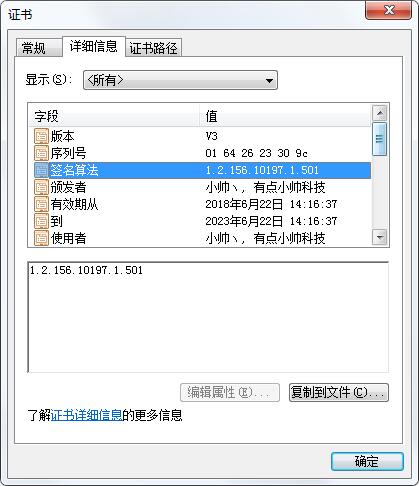
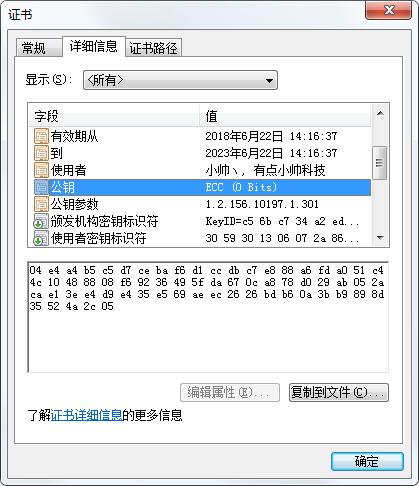
整理中。完全是Java代码调用BouncCastle生成的哦。先来个图看下 签名算法 和 公钥参数都是 符合SM2算法的
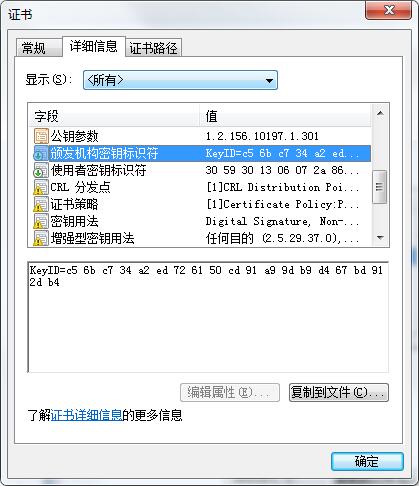
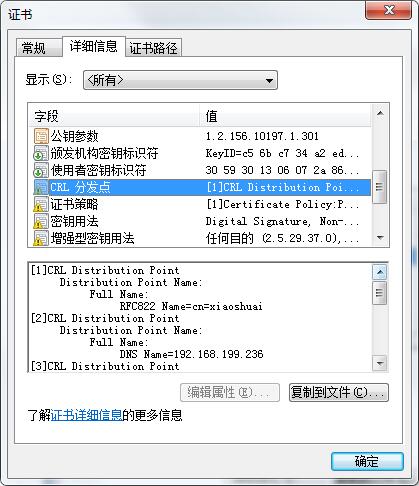
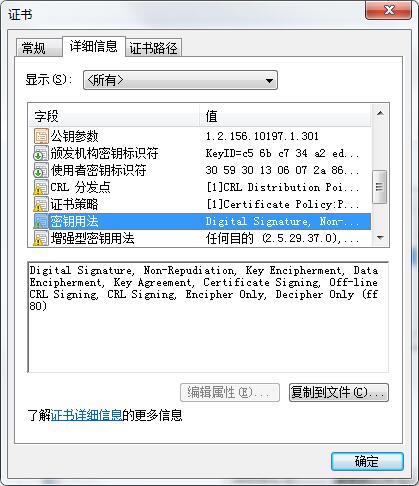
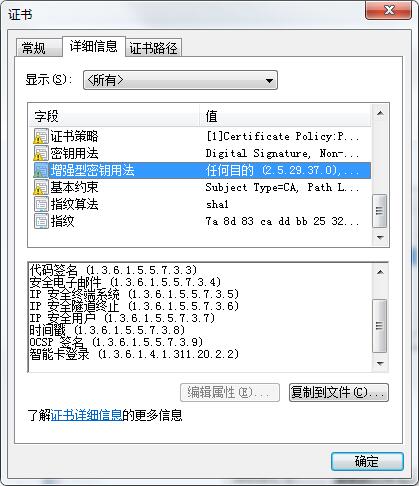
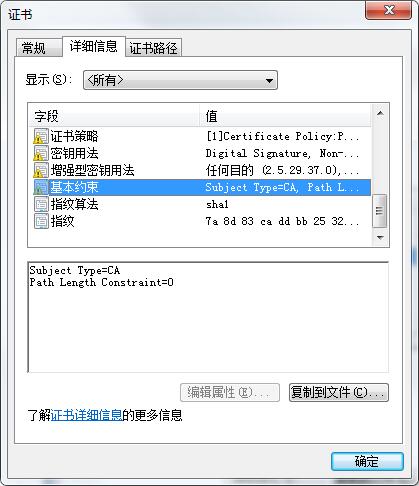
2018年6月22日更新:CRL分布点,添加证书策略,颁发者密钥标识,使用者密钥标识,密钥用法,增强密钥用法,基本约束

可以先加QQ 783021975 咨询相关问题。
2017年8月17日10:37:14 增加生成cer证书代码
/** * 国密证书签名算法标识 */ private static String SignAlgor = "1.2.156.10197.1.501"; /** * 生成国密ROOT证书方法 * @param pageCert.getCn()+","+ * @throws Exception */ public static void genSM2CertByRoot() throws Exception { SimpleDateFormat format = new SimpleDateFormat("yyyy-MM-dd HH:mm:ss"); org.bouncycastle.jce.provider.BouncyCastleProvider bouncyCastleProvider = new org.bouncycastle.jce.provider.BouncyCastleProvider(); Security.addProvider(bouncyCastleProvider); //证书的名称 String fileName = "root"+new Date().getTime()/1000; String path = "保存的路径"; String rootCertPath = path+fileName+".cer"; try { KeyPair kp = KeyGenUtil.getKeyPair2SM2(path,fileName);//这块就是生成SM2公私钥对 https://zb.oschina.net/service/70e3fdaf699a724b System.out.println("=====公钥算法====="+kp.getPublic().getAlgorithm()); BCECPrivateKey bcecPrivateKey = (BCECPrivateKey) kp.getPrivate();//使用ECPrivateKey PrivateKey都可以 BCECPublicKey bcecPublicKey = (BCECPublicKey) kp.getPublic();//使用ECPublicKey PublicKey都可以 //申请服务器证书信息 我是通过网页得到传递的参数 。如果测试 写死即可。这一步没有什么的。 X500Principal principal = new X500Principal("CN=小帅丶博客,O=小帅丶博客"); //X500Principal principal = new X500Principal("CN="+pageCert.getCn()+",O="+pageCert.getO()); X509V3CertificateGenerator certGen = new X509V3CertificateGenerator(); certGen.setSerialNumber(BigInteger.valueOf(System.currentTimeMillis())); certGen.setIssuerDN(principal);certGen.setNotBefore(new Date()); certGen.setNotAfter(CertAuthAssist.getYearLater(5)); certGen.setSubjectDN(principal); certGen.setSignatureAlgorithm(SignAlgor); certGen.setPublicKey(bcecPublicKey); //添加CRL分布点 QQ:783021975 certGen.addExtension(Extension.cRLDistributionPoints, true, XSCertExtension.getCRLDIstPoint()); //添加证书策略 QQ:783021975 certGen.addExtension(Extension.certificatePolicies, true, new DERSequence(XSCertExtension.getPolicyInfo())); //颁发者密钥标识 DigestCalculator calculator = new BcDigestCalculatorProvider().get(new AlgorithmIdentifier(OIWObjectIdentifiers.idSHA1)); X509ExtensionUtils extensionUtils = new X509ExtensionUtils(calculator ); certGen.addExtension(Extension.authorityKeyIdentifier, false, extensionUtils.createAuthorityKeyIdentifier(publicKeyInfo)); //使用者密钥标识 certGen.addExtension(Extension.subjectKeyIdentifier, false,extensionUtils.createSubjectKeyIdentifier(publicKeyInfo)); //密钥用法 QQ:783021975 certGen.addExtension(Extension.keyUsage,true,XSCertExtension.getKeyUsage()); //增强密钥用法 QQ:783021975 certGen.addExtension(Extension.extendedKeyUsage,true,XSCertExtension.getExtendKeyUsage()); //基本约束 BasicConstraints basicConstraints = new BasicConstraints(0); certGen.addExtension(Extension.basicConstraints, true, basicConstraints); X509Certificate rootCert = certGen.generateX509Certificate(bcecPrivateKey, "BC"); FileOutputStream outputStream = new FileOutputStream(rootCertPath); outputStream.write(rootCert.getEncoded());outputStream.close(); } catch (Exception e) { logger.info("======根证书申请失败"+e.getMessage());return null; }} 自愿购买 有需要请加QQ:783021975
CertAuthAssist.getYearLater()方法:
/** * 计算当前时间的N年后 * @param later 正整数 * @return */ public static Date getYearLater(int later) { Date date = new Date(); try { Calendar calendar = Calendar.getInstance(); calendar.add(Calendar.YEAR,later); date = calendar.getTime(); } catch (Exception e) { System.out.println(e.getMessage()); } return date; } 本项目支持
1.生成RSA算法cer证书 2.SM2算法cer证书。 3.生成根证书。子证书。三级证书 4.字符串公私钥转 公私钥对象 支持SM2算法
需要用到的BC包
org.bouncycastle bcpkix-jdk15on 1.57 org.bouncycastle bcmail-jdk15on 1.56
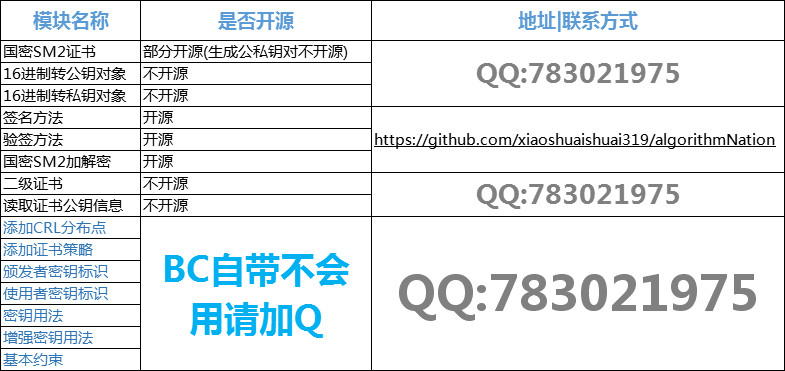
模块说明